Adding and Removing Users from Teams
Adding and Removing Users from Teams
Teams are only as useful as the users assigned to them. Adding the right users to the right teams ensures accurate routing, appropriate access, and seamless workflow logic across your platform.
There are two primary ways to assign users to teams:
- Manually, through the Console
- Automatically, via SSO group mapping
Each method has its place—manual management is great for small teams or initial setup, while SSO integration is essential for scaling with centralized identity systems.
Removing users from teams can also be done manually at any time. However, if your users are provisioned via SSO or an external identity provider, team membership should be managed through that system to avoid conflict during re-syncs.
In the sections below, we’ll walk through both methods and offer guidance for safe updates and removals.
Manually
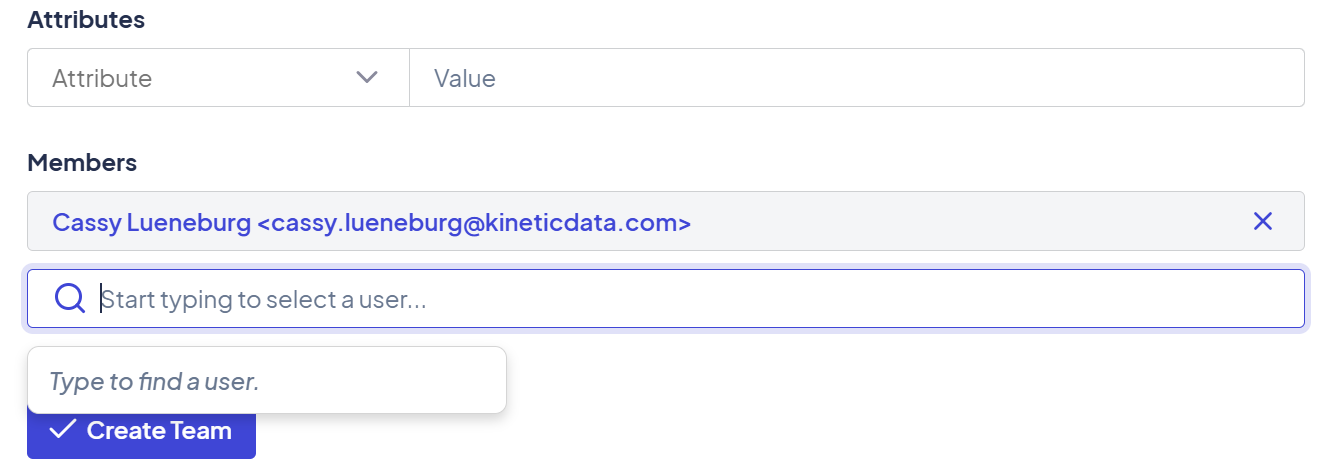
From the team page, use the Members option to search and assign users directly.
Adding Users to Teams via SSO
When using SSO (Single Sign-On) to manage user authentication and provisioning, you can also automate team membership by mapping group or organizational data from your identity provider (IdP) into Kinetic Data’s team structure.
This isn’t automatic. Team assignment must be configured during your SSO integration setup.
How It Works
When a user logs in via SSO for the first time:
- The SSO system sends profile information (e.g., email, username, department, groups).
- Kinetic receives this data and creates or updates the user profile.
- If properly mapped, group/team information from the SSO response can populate the correct team attributes or assignments in Kinetic.
- The user is then automatically added to the appropriate team(s), as long as those teams already exist in KD.
Requirements for Team Assignment via SSO
To successfully assign users to teams through SSO, you need:
1. Teams Created in Kinetic
Teams must already exist in the Kinetic Platform. The system does not auto-create teams based on incoming SSO data.
Create the exact team slugs you expect to receive from your SSO provider.
2. Attribute Mapping During SSO Configuration
This is the critical step. During your SSO setup:
- Identify which field in the SSO user profile (e.g.,
groups,department,team_ids) holds team membership data. - Map that field to the appropriate user attribute in Kinetic.
- Ensure the value matches an existing team slug or known team attribute value in KD.
For example, if the SSO
groupsfield returnsIT_Support, and KD has a team with slugIT_Support, the user will be matched to that team if mapped correctly.
Example Scenario
A user logs in via SSO. Their SSO profile contains:
{
"email": "[email protected]",
"name": "Alex Smith",
"groups": ["IT_Support", "SysAdmins"]
}
During SSO setup:
- The
groupsattribute is mapped to the team_membership attribute in KD. - KD has teams named IT_Support and SysAdmins.
- The user will automatically be added to both teams.
Important Considerations
- This mapping must be done during initial SSO setup; it is not automatic.
- If the SSO group name does not match an existing KD team, the user will not be assigned to a team.
- Any future updates to team structures in SSO must be manually reflected in KD (new team creation, renaming, etc.).
- Team membership updates typically occur at first login or on subsequent SSO-driven syncs.
Best Practices
- Align your SSO team/group structure with how you want to organize routing and access in KD.
- Create all necessary teams in KD before onboarding users via SSO.
- Work with your IdP administrator to ensure consistent attribute naming and reliable group values.
Related Topics
Updated 4 months ago
